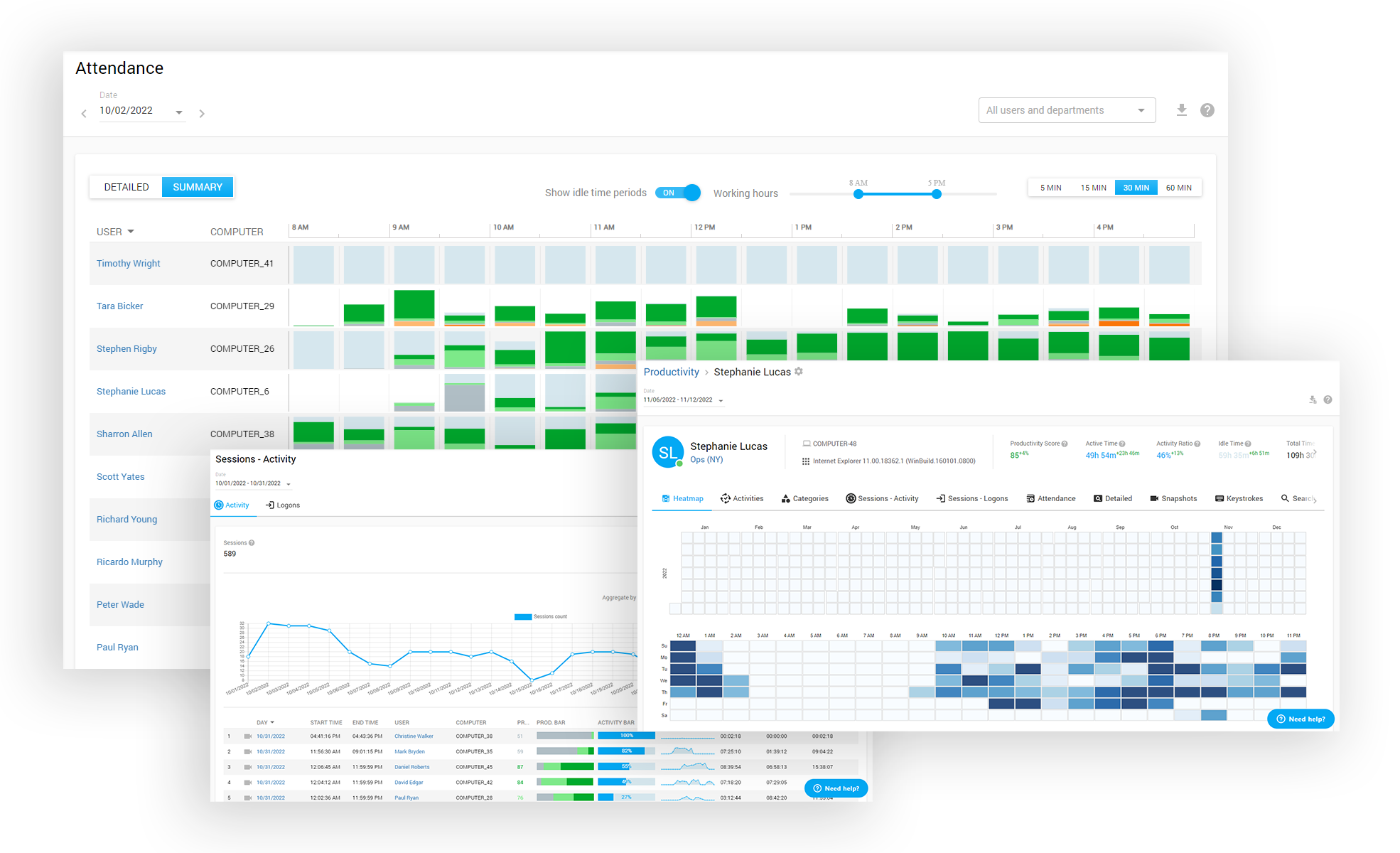
User Behavior Analytics
Respond to modern cybersecurity challenges with strong protective measures based on reliable User and Entity Behavior Analytics. Use smart Controlio’s algorithms, comprehensive statistics, and advanced data processing to shield your business from insider and outsider threats.

Agent Workload Forecasting
Controlio provides tons of historical data to predict spikes and dips in workloads and better respond to customer demand.
Automated Web/App Categorization
The Controlio engine allows classifying web pages and applications for labeling or blocking with little to no tedious manual manipulations.
Offline Data Collection
Controlio stores data locally on employees’ computers and uploads them to the Dashboard as soon as the internet connection is restored.
How UEBA Delivered by Controlio Can Save You
from Data Leaks, Damaged Reputation, and Money Loss
Separate normal user behaviors from suspicious anomalies and spot credential theft, fraud, data exfiltration, and other malicious activities more efficiently. Launch immediate responses to unusual actions and even anticipate security issues by patching up possible holes.






What Are Controlio Features?





Departments hierarchy
Live sessions monitoring
Remote client agent deployment
Multi-login Dashboard with access control list
Data Export to PDF, CSV
Agent Stealth mode and Icon mode
Audit Log (tracks activities inside the Dashboard)
2-Step Authentication
Cloud-based, on-premises, private AWS cloud deployment options
GDPR data recording&view mode
API for data integration
Active Directory OUs and users synchronization
Reviews
What our customers are saying
“EFFECTIVE DATA MONITORING, INSIGHTS AND ANALYSIS”

"I like the option set 'do not track' for specific users and flexibility to adjust licensing for data collection. Also the ability to group users for analyzing productivity at the group, company, or individual level is incredibly beneficial."
April 20, 2025
Senior Project Manager, Medical Devices, 51-1000 employeesUsed the software for: 6-12 months
“IMPROVES PRODUCTIVITY BY A HUGE MARGIN”

"Tracking accurate times for any app that was difficult before and it doesn't slow down our systems and the alerts for unauthorized access keep our data secure."
July 23, 2025
Marketing Specialist, Marketing and advertising, 11-50 employeesUsed the software for 1-5 months
“THE BEST TIME TRACKING SOFTWARE”

"It is incredibly user-friendly, you can download it quickly and access excellent customer support for any issues encountered."
May 24, 2025
Group IT Director, Transportation/Trucking/Railroad, 51-1000 employeesUsed the software for 1-2 years







