Proactive Protection of
Federal Information Systems for Government and Public Agencies
Counter cyber threats and stay compliant with federal, local,
and international requirements while boosting operational performance.

Tough Security
Controlio uses reliable encryption, offers two-step authentication, and allows blacklisting IPs to guarantee the highest possible data security.
Immutable Audit Trail
The app maintains forensic-level logs recording every user action in the system to respond to compliance audits and ensure thorough security investigations.
Smart Engine and Vast Database
Controlio comes with the opportunity to automatically categorize websites and applications according to their subjects and assign 5 productivity levels.
How Controlio Implements Best Practices for Safeguarding
the Government’s Sensitive Information and Citizens’ Personal Data from Cyberattacks
Reveal hidden security gaps and insider threats to shield classified data and other protected information from misuse and malicious intent. Put into effect preventative, detective, and corrective security controls packed into a single solution.





What Are Controlio Features?

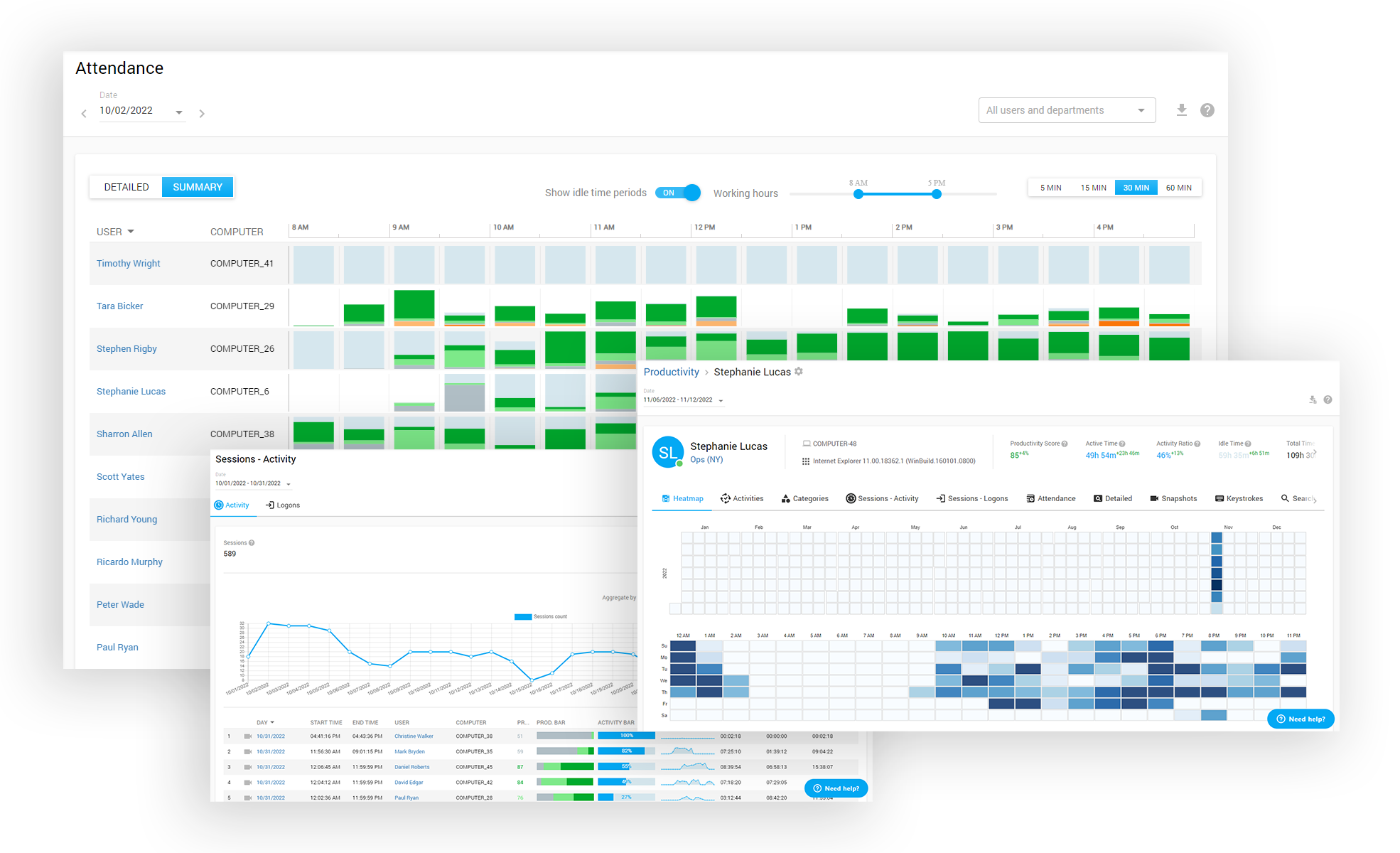




Departments hierarchy
Live sessions monitoring
Remote client agent deployment
Multi-login Dashboard with access control list
Data Export to PDF, CSV
Agent Stealth mode and Icon mode
Audit Log (tracks activities inside the Dashboard)
2-Step Authentication
Cloud-based, on-premises, private AWS cloud deployment options
GDPR data recording&view mode
API for data integration
Active Directory OUs and users synchronization
Reviews
What our customers are saying
“EFFECTIVE DATA MONITORING, INSIGHTS AND ANALYSIS”

"I like the option set 'do not track' for specific users and flexibility to adjust licensing for data collection. Also the ability to group users for analyzing productivity at the group, company, or individual level is incredibly beneficial."
April 20, 2025
Senior Project Manager, Medical Devices, 51-1000 employeesUsed the software for: 6-12 months
“IMPROVES PRODUCTIVITY BY A HUGE MARGIN”

"Tracking accurate times for any app that was difficult before and it doesn't slow down our systems and the alerts for unauthorized access keep our data secure."
July 23, 2025
Marketing Specialist, Marketing and advertising, 11-50 employeesUsed the software for 1-5 months
“THE BEST TIME TRACKING SOFTWARE”

"It is incredibly user-friendly, you can download it quickly and access excellent customer support for any issues encountered."
May 24, 2025
Group IT Director, Transportation/Trucking/Railroad, 51-1000 employeesUsed the software for 1-2 years





